E-time | the software company
E-time with Cocomero: a gesture for the Palestinian people
E-time promotes a vision based on universal human values, such as solidarity, compassion and justice, in defense of innocent civilians affected by conflicts.
In our small way, we felt it was important to support and stand alongside the Cocomero initiative.
Cocomero is a spontaneous volunteer project led by a group of food bloggers, aiming to raise funds for Palestinian civilians left without homes and means of livelihood due to bombings and forced displacements following October 2023
The project began in 2024 with the first ebook. In 2025, the second ebook, “Cocomero & Friends – Recipes and Voices for Palestine” was launched.
It is not just about cooking, but about culture, memory, and identity: a simple, everyday way to tell the story of a people through what they prepare, preserve, and pass down, even in the most difficult times. For more information about the initiative, visit the project link
“Remembering a child being born, it becomes our duty to care for the children who die every day”
E-time at Forum PA 2025
E-time will be participating in FORUM PA 2025, taking place from May 19 to 21 at the Palazzo dei Congressi in Rome. This key event, dedicated to innovation in the Public Administration, will focus on the theme: “Towards an Augmented Public Administration: People, Technologies, Relationships.”
FORUM PA is Italy’s leading event focused on innovation in the Public Sector. Organized annually by FPA, a company of the Digital360 Group, it brings together institutions, businesses, and citizens to promote the modernization of public services through digital technologies, training, and open dialogue on public policies.
During the event, E-time will showcase its advanced digital solutions, designed to support the digital transformation of the Public Administration by integrating intelligent technologies and promoting more agile, collaborative operational models.
Join the seminar on May 20
In addition to its presence at the exhibition area, E-time will lead a dedicated seminar on May 20 at 12:30 PM in Room 4, titled: “AI Agents Serving Citizens: The AIFA Case Study.” This session will explore how AI agents can improve citizen interaction by offering fast, personalized, and reliable responses.
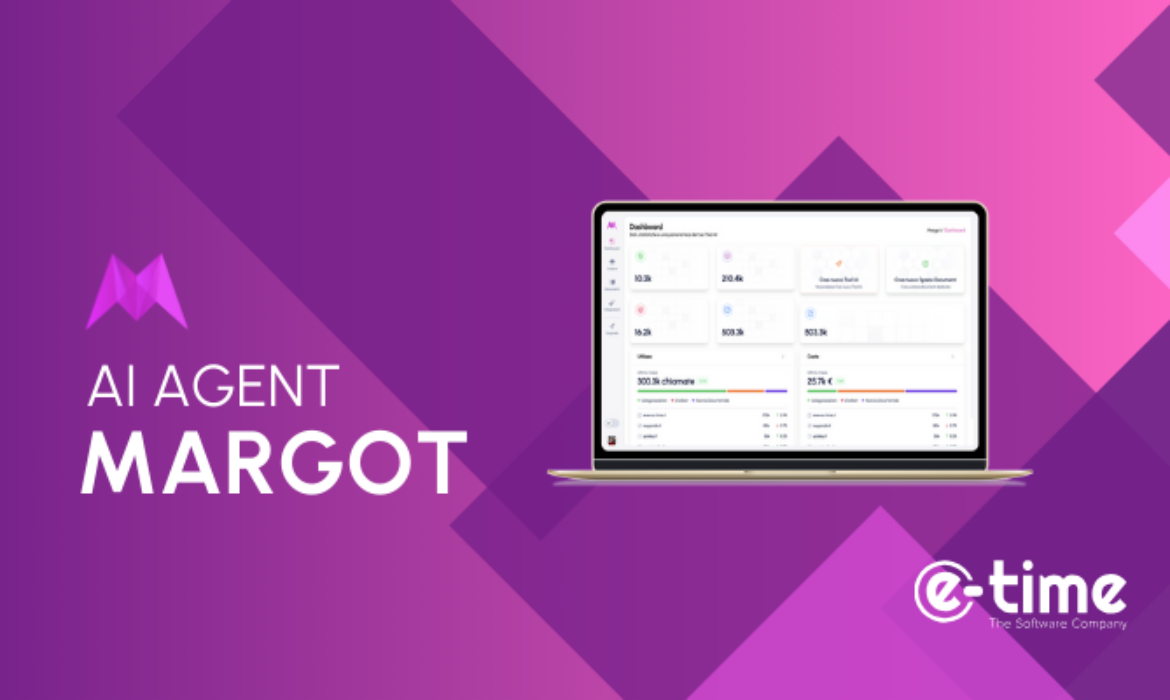
At the heart of the seminar will be Margot, the latest AI-powered solution developed by E-time to support the digital evolution of the Public Administration.
Margot not only simplifies communication—ensuring transparency and trust in the information provided—but also allows public sector employees to focus on higher-value tasks. You can register and join the seminar at this link.
It will be a great opportunity to share experiences, engage with industry experts, and contribute to the ongoing dialogue on the future of public services.
We look forward to seeing you at booth 2D!
Margot, E-time’s new AI Agent working by your side!
The wait is over! After a testing phase, Margot is now officially part of the E-time offering. Margot is the AI Agent that learns, analyzes, and acts to improve and optimize work across all areas of your business.
Margot is an agent that can assist with daily tasks and adapt to the operational needs of the client, seamlessly integrating into daily workflows. It’s an advanced AI-driven solution designed to simplify complex tasks, enhance productivity, and provide continuous, personalized support.
Thanks to its flexible and modular architecture, Margot is an intelligent, versatile tool that can be perfectly integrated within the company ecosystem. Its potential is expressed through a wide range of features: AI chatbots, classifiers, virtual assistants, and knowledge-based search tools.
Designed to ensure scalability and ease of configuration, Margot represents a strategic innovation for the digital infrastructure of organizations aiming to accelerate their technological transformation and keep up with ongoing change.
Visit the Margot page for more information
New E-time headquarters!
E-time is moving! Our new Verona headquarters is now located at Viale del Lavoro, 33 in San Martino Buon Albergo (VR).
We’ve finally completed work on our new spaces, which will allow us to offer an even more welcoming environment to both our E-timers and our clients.
What is the difference between an AI Agent and a Chatbot?
What are AI Agents and how do they work
AI agents are software programs capable of autonomously understanding and responding to user requests or performing tasks on behalf of individuals or other systems. They make decisions based on data and natural language processing (NLP).
In most cases, AI agents utilize large language models (LLMs), which enable them to process and analyze data from various sources. They leverage external tools such as APIs, online searches, and databases to access up-to-date information and optimize their performance.
AI agents continuously improve by learning from each interaction. This ongoing learning process allows them to refine their capabilities and adapt to the evolving needs of users.
What is an Chatbot
A chatbot is a software application designed to simulate written or spoken interactions with users. Traditional chatbots primarily provide predefined responses to a limited set of questions. Since they lack natural language comprehension, they are often rigid and struggle to adapt to user needs.
More advanced chatbot versions incorporate techniques such as natural language processing (NLP) and natural language understanding (NLU). These advancements have made chatbots more sophisticated, enabling them to better understand and respond to user intent.
Today, chatbots are widely used across various industries, from customer support to business automation, with the goal of providing instant responses, streamlining processes, and enhancing the user experience.
The main differences between AI agents and chatbots
When comparing AI agents and chatbots, fundamental differences emerge in how they interact with users. These distinctions can be categorized as follows:
- Understanding User Intent
Traditional chatbots operate based on predefined rules and standardized responses, relying on keyword recognition and offering only a limited understanding of context and language nuances.
Conversely, AI agents utilize advanced language models to analyze user intent and context more deeply, enabling smoother and more natural interactions. - Learning Capability
AI agents can learn from interactions and continuously improve over time, evolving through experience and new information.
Traditional chatbots, on the other hand, lack autonomous learning capabilities and require manual updates to handle new queries or workflow modifications. - Handling Complex Tasks
Chatbots are effective in executing simple, repetitive tasks but struggle with managing more complex and multi-step requests.
AI agents, however, are designed to tackle complex problems, make informed decisions, and, in some cases, act autonomously. - Personalization and Context Awareness in Interactions
AI agents can tailor responses based on interaction history and user preferences, providing a more personalized experience.
In contrast, traditional chatbots offer minimal personalization, typically relying on basic information without considering past interactions.
How to use AI Agents in customer support
The integration of AI agents in customer support is transforming service management, making it faster, more accurate and personalized.
Here are some examples where their use is particularly effective:
- Personalized Support
Thanks to memory of past interactions, AI agents can offer personalized responses by using customer preferences and adapting solutions to their specific needs. - Intelligent Request Routing
AI can automatically and in real-time assign requests to the most appropriate departments, reducing wait times and optimizing the use of company resources. - Conversation Analysis and Continuous Improvement
AI agents analyze interactions to improve the responses provided, identify common issues, and optimize customer service.
E-time with Palestine Red Crescent Society
E-time emphasizes universal human values, such as solidarity, compassion, and justice for the innocent civilians who are victims of the ongoing Israeli-Palestinian conflict.
In such a delicate historical moment, we have been struck by some data extracted from the Amnesty International investigations into the ongoing conflict, including:
- As of October 7, 2024, over 42,000 Palestinians have died, including over 13,300 children, and more than 97,000 have been injured;
- 1.1 million people have been evacuated;
- Approximately 625,000 students have lost an entire academic year.
To lend a hand, no matter how small, we have decided to support Friends of the Palestinian Red Crescent Society, a humanitarian organization that provides medical, health, and social assistance to the Palestinian population, both in the Palestinian territories and in neighboring countries.
The organization is part of the International Red Cross Movement, and its main purpose is to support the population through healthcare assistance, emergency interventions in the field, health promotion, and social support.
E-time ISO 27001 certified.
The certifications acquired by E-time
We are proud to announce that E-time has achieved the UNI CEI EN ISO/IEC 27001:2024 certification. This international standard establishes the requirements for an Information Security Management System (ISMS), ensuring a structured approach to data protection.
Below is a list of all certifications E-time has obtained under ISO/IEC 27001:
- Cert. no. 84671 UNI CEI EN ISO/IEC 27001:2024 – Information security, cybersecurity, and privacy protection – Information security management systems – Requirements.
- Cert. no. 84673 ISO/IEC 27018:2019 – Information technology — Security techniques — Code of practice for the protection of personally identifiable information (PII) in public clouds acting as PII processors.
- Cert. no. 84674 ISO/IEC 27017:2015 – Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services.

E-time has always prioritized data security and, over the years, we have implemented internal procedures to protect it. By obtaining this certification, we have chosen to implement these processes in compliance with the standards set by ISO 27001, validated by an authorized third-party body.
What Changes After Obtaining Certification
Achieving this certification has several implications and entails specific operational responsibilities for the company, including:
- Risk identification and management: the organization must mitigate risks related to information security, preventing and monitoring them continuously.
- Implementation of an Information Security Management System: Introducing a set of procedures and controls to ensure the protection of confidentiality, integrity, and availability of information.
- Compliance with legal and regulatory requirements: Adhering to information security provisions and current regulations, primarily GDPR.
- Implementation of the PDCA (Plan-Do-Check-Act) cycle: ensuring continuous improvement of the ISMS, which involves periodic internal audits, management reviews, and updates to controls.
What This Means for Our Clients
Achieving certification guarantees the validity of ongoing processes for information security and data protection, reducing the likelihood of incidents related to data breaches or cyberattacks.
By reaching this milestone, E-time reinforces its tangible commitment to maintaining the highest standards of information security.
The certifications can be fully reviewed at this link.
Explore our solutions for Identity and Access Management
Chatbot & AI: a new Partnership between E-Time and Botpress Is Born
We are pleased to announce the launch of a new strategic collaboration with Botpress one of the most advanced platforms for creating and managing chatbots on the market.
The partnership between E-Time and Botpress will lead to the integration of Botpress into our services (integration with Rexpondo is already available), allowing us to leverage the potential of artificial intelligence (AI) and natural language processing (NLP).

Botpress integrates AI into its chatbots through an advanced modular architecture that enables the use of NLP and machine learning to create smarter and more personalized interactions.
The partnership between E-Time and Botpress combines E-Time’s technological know-how with the capabilities of an innovative and constantly evolving platform.
This growth-oriented collaboration has the shared goal of providing companies with advanced tools to enhance user experience, automate customer service, and optimize internal processes.
E-time with Rete Dafne against every form of violence

It’s time to reveal our second “Useful Gift” for Christmas 2023.
The events of the last months of 2023 have received significant media attention, bringing the issue of gender-based violence back into the spotlight, which remains a real scourge in Italy and beyond.
Therefore, we have chosen to make our small contribution to Rete Dafne, which daily provides support and assistance to victims of gender-based violence, and not only because the work of Rete Dafne concerns all victims of any type of crime.
For further information about the valuable work carried out by this association, we refer you to their website: retedafne.it
E-time is participating in the Plastic Pull project.
This Christmas, we have focused on two themes that are very important to us, and one of them is the Environment.
E-Time has contributed to collecting 37 kg of waste abandoned on beaches, in parks, and on streets, requalifying degraded ecosystems in Italy located in areas where local administrations do not intervene. All of this has been made possible thanks to the Plastic Pull project by Piantando.

The project
Plastic Pull is one of Piantando’s social and environmental impact projects, with the goal of recovering tons of scattered waste throughout Italy, leveraging its network of associations and initiatives.
After identifying the areas of degradation to intervene, Piantando coordinates the intervention with field contacts. Each collected bag is certified, including photographs, location and date of collection, weight, disposal method, and the operational team.
Who is Piantando

Piantando is a Benefit company that initiates social and environmental impact projects worldwide by collaborating with companies of all sectors and sizes. The central focus of Piantando’s work is transparency and sustainability, which characterize each project and ensure its proper development.
Below is the link where you can find more information about the project supported by E-time and our contribution: E-time X Plastic Pull