E-time | the software company
NIS2 Obligations in the Healthcare Sector: practical tools for compliance
How NIS 2 strengthens the resilience of hospital IT systems
The NIS2 Directive establishes a strategic framework aimed at ensuring operational continuity and digital resilience of healthcare facilities, with the goal of creating a safer European ecosystem capable of withstanding cyberattacks and protecting critical infrastructure.
To achieve these objectives, NIS2 promotes a proactive approach to risk management, which includes continuous vulnerability assessments and the implementation of structured security plans, thereby ensuring uninterrupted operation of essential healthcare services.
Key practices to strengthen security include continuous system monitoring, penetration testing, network segmentation, the adoption of the Zero Trust model, and tools for secure digital onboarding and identity verification.
Which healthcare facilities fall under the scope of NIS 2?
The NIS2 Directive sets out uniform criteria to identify public and private operators considered “essential” or “important” within critical or high-criticality sectors, including healthcare, establishing obligations for all parties involved.
The regulation particularly applies to:
- traditional healthcare systems and Digital Health;
- hospitals, clinics, laboratories and healthcare service providers.
- The scope also covers the entire healthcare supply chain, including manufacturers, suppliers, and laboratories, as well as related sectors, ensuring comprehensive and consistent protection of critical infrastructure.
Obligations of hospitals and clinics under NIS2
The NIS2 Directive establishes stricter requirements for cybersecurity and risk management in healthcare facilities. Among the main obligations is the strengthening of ICT measures through advanced tools, such as multi-factor authentication (MFA) and advanced encryption.
Facilities must also develop risk management plans, continuously assess threats, and monitor systems to detect anomalies, promptly activating incident response procedures. It is essential to notify any breaches to the competent authorities and ensure continuous staff training, with clearly defined responsibilities at all levels of the organization.
Rexguard: comprehensive management of security incidents
Rexguard is an integrated platform designed to simplify the management of security incidents, vulnerabilities, non-compliance issues, and audits by bringing all these processes together in a single centralized environment. The platform leverages automated workflows that enable immediate action on events, covering the entire incident lifecycle from detection to final resolution.
In addition to speeding up incident response, Rexguard helps organizations maintain compliance with standards and regulations such as NIS2, ISO 27001, and DORA. Thanks to full activity traceability, detailed audit trails, and customizable reports, companies can accurately monitor every stage of incident management, strengthening overall IT security and governance.
Kubernetes: efficiency and scalability for organizations
Kubernetes: what It is and what it’s for
Kubernetes is an open-source platform designed to orchestrate containers and simplify the management of applications and services in an automated and scalable way.
Applications are divided into one or more containers, which Kubernetes groups into pods, the fundamental execution units of the system. Each pod can contain multiple containers that share resources and common settings.
Pods run on nodes, which are physical or virtual machines forming the cluster infrastructure.
Kubernetes automates complex operations and manual processes required for deployment, monitoring, and error management, ensuring that applications remain stable, operational and high-performing at all times.
How a Kubernetes Cluster works
A Kubernetes cluster represents an active instance of the orchestration platform. It is composed of two fundamental elements: the control plane and a set of worker nodes.
The control plane is responsible for managing and maintaining the cluster’s desired state, ensuring that the defined configuration is enforced. The nodes, on the other hand, are the operational units that run the applications and associated workloads.
Administrators define the desired state by specifying which applications should be deployed, which container images to use, the resources to allocate, and the configurations required for the system to function correctly.
Benefits of adopting Kubernetes
Adopting Kubernetes provides significant advantages in managing complex, dynamic and highly scalable IT environments. The main benefits include:
- Efficient management of complex environments:
Kubernetes is particularly suited for scenarios where it is necessary to deploy and manage multiple containers across several hosts, providing centralized and automated control. - Automatic scalability:
The platform dynamically adjusts resource allocation based on workload, ensuring optimal performance and more efficient use of costs. - Separation between development and operations:
It promotes process automation, simplifies collaboration between Dev and Ops teams, and accelerates the application release cycle while maintaining stability in production. - High portability:
Kubernetes can run on various types of infrastructure , from on-premises environments to public and private clouds , ensuring consistency in commands and uniformity in operational processes. This feature allows deployment in any cloud environment, using the same tools and methodologies regardless of the underlying platform.
Yookey: Keycloak managed in SaaS
Yookey is an Identity and Access Management (IAM) solution based on Keycloak, offered as a Software as a Service (SaaS) and fully managed.
The platform provides a secure, constantly updated, customizable, and GDPR-compliant environment, simplifying the management of digital identities.
The service independently manages the entire Keycloak lifecycle combining Keycloak’s native functionalities with the convenience of a ready-to-use solution.
In this way, Yookey eliminates operational complexity for the end user, allowing organizations to focus on their applications without worrying about the underlying infrastructure.
NIS2 e DORA: obligations, differences and how to comply
Who do DORA(Digital Operational Resilience Act) and NIS2 apply to?
The DORA Regulation targets operators in the financial sector. This includes a wide range of entities such as banks, insurance companies and investment firms, as well as critical ICT providers, for example cloud services and data centers that support the activities of financial intermediaries.
The NIS2 Directive, on the other hand, has a much broader scope. It covers strategic sectors in both the public and private spheres, including energy, transport, healthcare, digital infrastructure, and public administrations. Within this framework, operators are classified as Essential Entities (EE) or Important Entities (IE), based on criteria such as organizational size and economic volume.
When a financial entity falls under both regulations, the provisions of DORA take precedence, serving as a specialized framework over the general rules established by NIS 2.
What are the differences between DORA and NIS2
Although both DORA (Digital Operational Resilience Act) and NIS 2 share the primary goal of strengthening digital resilience and cybersecurity in the EU, they differ in their characteristics and scope of application.
The main distinctions:
- Legal form: DORA is a regulation, directly applicable in all Member States without the need for national transposition, ensuring uniform implementation. NIS 2, on the other hand, is a directive, which sets out general objectives but allows individual countries the flexibility to transpose them into national law, potentially resulting in differences in interpretation and application.
- The scope of application: DORA focuses specifically on the financial sector, providing a specialized framework for banks, insurance companies, funds, and critical ICT providers. NIS 2 has a broader scope, covering a wider range of designated entities.
- Finally, DORA stands out for its high level of operational detail and precision in its requirements for digital resilience, to the extent that it can serve as a practical reference for implementing NIS 2 requirements within the financial sector.
ICT Risk Management under NIS2 and DORA
Both DORA and NIS 2 impose strict obligations for ICT risk management, with the aim of strengthening the digital resilience of organizations. Both regulations emphasize the need for a governance model that integrates cybersecurity into corporate strategies and assigns direct responsibilities to executive bodies.
Regarding ICT risk, DORA adopts a highly structured approach, requiring the implementation of comprehensive risk management frameworks, the development of business continuity plans and disaster recovery strategies, and the establishment of proactive procedures to monitor and mitigate risks associated with third-party providers.
For ICT risk management, the NIS 2 directive sets out mandatory minimum measures, with particular attention to the security of suppliers and the supply chain. On the incident reporting side, the regulation establishes strict obligations, requiring the prompt notification upon detection of significant events.
Incident Reporting Requirements under NIS2 and DORA
Both NIS 2 and DORA define clear obligations for the management and reporting of security incidents.
NIS 2 requires that security incidents be reported to the competent authorities, sending a preliminary alert to the CSIRT (Computer Security Incident Response Team) within 24 hours of discovering the event and submitting the official notification within 72 hours of the incident.
DORA, on the other hand, establishes a more detailed and stringent reporting process for the classification, management and notification of ICT incidents, aiming to ensure that financial infrastructures can remain operational and resilient even in the event of severe attacks.
Rexguard: the solution for Regulatory Compliance
Rexguard is a GRC (Governance, Risk & Compliance) platform designed to centrally and seamlessly manage all aspects of digital security. It supports the handling of incidents, vulnerabilities, non-conformities, corrective actions and audits, providing a comprehensive and integrated overview of an organization’s security posture.
Through workflow automation and a structured approach to process management, Rexguard enables rapid incident response, continuous monitoring of ICT risks and effective oversight of all activities required to meet regulatory obligations.
In particular, the platform facilitates compliance with NIS 2 and DORA, offering tools for risk management, supply chain security and mandatory reporting to supervisory authorities.
Discover E-time’s GRC Platform
AI Chatbot and Ticketing Systems: optimizing Customer Support
AI Chatbots in ticket management systems: role and functionalities
The integration of AI chatbots into ticketing systems allows for optimizing the management of support requests by reducing response times and automating crucial tasks such as classification, assignment and prioritization.
Some of the most relevant capabilities include:
- Automatic ticket categorization;
- Semantic and customer sentiment analysis;
- Generation of predefined or dynamic responses.
Thanks to these features, many recurring requests can be handled autonomously, leaving human staff to focus on more complex cases and strategic decisions.
How the integration of AI chatbots in a ticketing system works
AI chatbots combine machine learning algorithms with Natural Language Processing (NLP) and next-generation language models (LLMs) to accurately interpret the content of support requests.
These solutions enable the system to understand natural language, identify user intent, and detect emotional state. A further step is represented by Retrieval-Augmented Generation (RAG), which expands the context for analysis and allows for the generation of more relevant and personalized responses.
A key aspect is the ability for continuous learning: by analyzing previous interactions, the AI progressively refines its responses, improving overall ticket management.
Why adopt AI chatbots in support systems
The implementation of AI chatbots within ticketing systems brings numerous operational and strategic advantages:
- Improved efficiency: reduced response times and faster resolution of requests.
- Support scalability: handling increasing volumes of tickets without proportionally increasing the number of agents.
- Team relief: automation of repetitive tasks, allowing staff to focus on more complex issues.
- Optimized customer experience: timely, personalized responses and always-available self-service options.
Moreover, AI enables actionable insights from the collected data, monitoring service performance, anticipating potential issues, and ensuring a proactive approach consistent with the brand identity.
From AI to real support: the integration of Margot in ticketing systems
The integration between Margot, the AI agent developed by E-time and Rexpondo, the ITSM ticketing system, simplifies and makes support request management more efficient.
One of Margot’s main tools is the AI chatbot, which analyzes incoming tickets, automatically suggests the most appropriate classification and provides immediate, contextualized responses based on the company’s knowledge base.
Thanks to continuous learning, the agent constantly improves response accuracy, ensuring scalable, personalized and consistent support across all communication channels.
Discover the solutions offered by E-time
Gamification and Cybersecurity: the key to effective corporate training
What is Gamification and why does it work in corporate training
Gamification is a methodology that applies typical game mechanisms—such as points, levels, rewards, leaderboards, and challenges—to non-gaming contexts, particularly corporate training. The goal is to leverage the motivational power of games to make mandatory and repetitive activities more enjoyable, engaging, and productive.
This approach significantly increases employee engagement and enthusiasm, enhancing content understanding and improving the retention of information in long-term memory.
Gamification in Cybersecurity: How to make security more engaging
In the field of cybersecurity, human error is one of the main risks, often leading to breaches and data leaks. Employees are frequently unprepared to face increasingly sophisticated attacks such as phishing and ransomware.
Gamification addresses this challenge by turning cybersecurity training from passive to proactive, making it more engaging and effective. This approach helps foster a true security culture, raising employee awareness in a simple and interactive way.
Through tools like weekly challenges, leaderboards, and rewards, gamification encourages safe behaviors such as using strong passwords or reporting phishing attempts.
Benefits of Gamification in Cybersecurity Training
Integrating gamification into training programs, including those focused on IAM, enhances knowledge retention, boosts engagement, and reduces stress through interactive and secure learning. Gamified paths provide immediate feedback, foster collaboration and productivity, and allow for effective monitoring of progress and areas for improvement.
When applied to cybersecurity training, gamification turns an activity often seen as complex into an engaging and effective experience.
Key Benefits:
- Engagement and Motivation
Game dynamics make training more interesting, stimulating, and rewarding, increasing active participation. - More effective and lasting Learning
Through play, concepts are better absorbed and more easily transferred into long-term memory. - Security Culture and Behavioral Change
Gamification encourages best practices—such as creating strong passwords or reporting phishing attempts—promoting security-oriented behaviors. - Measurability and Adaptability
Gamified systems enable tracking results, identifying those who need support, and customizing learning paths. - Productivity and Workplace Climate
Beyond improving learning, gamification fosters collaboration, communication, and a safer, more proactive work environment.
Skillbay: LMS with Integrated Cybersecurity Module
Skillbay is an innovative LMS platform that revolutionizes corporate training through a modular, flexible environment designed to turn learning into an interactive experience with gamification and personalized learning paths.
Among its key features, Skillbay includes a preconfigured module dedicated to cybersecurity, developed to meet standards and regulations such as NIS2 and ISO 27001.
This module enables companies to immediately launch targeted programs to raise cybersecurity awareness and promote best practices, with the flexibility to adapt content to specific organizational needs.
Simplified Incident Response with Rexguard
How to Manage a Security Incident
The management of a cybersecurity incident begins with the identification of anomalous activities, continues with the analysis and containment of the event, and ends with the restoration of the compromised functionalities, accompanied by the implementation of actions aimed at the continuous improvement of security.
- Timely threat detection
The organization must have tools and procedures that are always active to promptly detect any signs of compromise, such as abnormal system behavior, unauthorized access, or suspicious malfunctions. - Incident analysis and assessment
Once a potentially suspicious event is intercepted, it is essential to analyze it to determine whether it is actually a security incident. The goal is to distinguish between false alarms and real threats that require an immediate response. - Containment and management actions
In the event of incident confirmation, containment measures must be promptly implemented to limit damage and prevent the issue from spreading to other systems or services. - Operational restoration
Once the emergency phase is over, the compromised functionalities are restored, ensuring that the systems are once again operational and secure. The incident is then formally closed, accompanied by detailed documentation of the activities carried out. - Review and continuous optimization
Following the closure of the incident, it is essential to conduct a retrospective analysis to draw useful lessons. Relevant information is shared with the interested parties, procedures are updated, and personnel are made aware, in order to strengthen the organization’s resilience and prevent similar events in the future.
What is an Incident Response Plan
To manage these phases in an optimized and effective way, it is useful to have a structured incident response plan that defines roles, responsibilities, and clear procedures to follow in case of emergency.
The Incident Response Plan is a strategic and operational document that defines the methods and procedures by which an organization must address cybersecurity events. It is designed to ensure a rapid and effective reaction to threats such as hacker attacks, data leaks, or system compromises.
The ability to respond promptly to incidents plays a crucial role in limiting damage and quickly restoring operational continuity.
The main goal of incident response is to identify, manage, and resolve security events, minimizing their impact on company data and operations.
Incident Management According to the NIS 2 Directive
Increasingly strict regulations, such as the NIS2 Directive, require organizations not only to implement formal procedures and internal guidelines for the management of security incidents, but also to promptly report any breaches to the competent authorities.
Among the obligations set out by the NIS2 Directive, a key requirement is the obligation to notify security incidents to the competent authorities, by sending a preliminary alert to the CSIRT (Computer Security Incident Response Team) within 24 hours of detecting the event, followed by the official notification within 72 hours of the occurrence of the cybersecurity incident.
Security Incident Management with Rexguard
Rexguard is an advanced platform that enables centralized management of incident response, vulnerabilities, non-conformities, and audits within a single integrated system. Thanks to automated workflows, the platform allows for rapid intervention on incidents, simplifying every phase of the event lifecycle, from initial detection to formal closure.
In this way, Rexguard not only accelerates the detection and resolution of incidents, but also supports compliance with regulatory standards such as NIS2, ISO 27001, and DORA, ensuring complete traceability, detailed audit trails, and comprehensive reporting.
Skillbay: the LMS platform for business training
In an ever-evolving and increasingly competitive job market, skills are the true driving force behind business growth. It is precisely from this awareness that Skillbay was created—the new LMS (Learning Management System) platform developed by E-time, designed to support companies in managing and developing internal skills.
The platform has been conceived to provide concrete and effective tools capable of enhancing skills, placing them at the core of business development, and turning them into a real competitive advantage.
Skillbay is designed to map, develop, and monitor employee skills, integrating seamlessly with business processes and making training an engaging and stimulating experience through the use of gamification.
Among its most relevant features for companies, Skillbay offers centralized training management with advanced tools for organizing educational content and continuously monitoring learning paths, also including a pre-loaded module dedicated to cybersecurity.
With Skillbay, training is no longer a mere requirement—it becomes a strategic lever for the development of human resources and the success of the organization.
Would you like more information?
Discover Skillbay an contact our sales team
Discover Skillbay an contact our sales team
AI and Public Administration: towards Intelligent Governance
What role does AI play in Public Administration
AI is emerging as a driver of change for Public Administration, fostering a structural transformation of public services. It offers the opportunity to make the relationship with citizens more efficient and innovative, introducing new management and interaction models.
Its potential impact lies in its ability to make public administration more effective, transparent, and accessible to all.
What are the benefits of integrating AI into Public Administration
Among the main benefits stemming from the integration of AI into public services, we find:
- Optimization of services and cost reduction:
Public Administrations can direct AI investments towards the automation of repetitive tasks related to institutional services and basic administrative functions. This makes it possible to free up resources to be allocated to higher value-added activities, contributing to the improvement of the quality of services offered to citizens. - Transformation of public service management:
AI is profoundly changing the ways public services are delivered and managed. By automating complex and repetitive processes, AI significantly reduces the operational workload, increases efficiency, and improves the accuracy of operations, minimizing human errors. - Enhancement of predictive and decision-making capabilities:
AI strengthens the ability of public administrations to analyze data in an advanced way, improving the quality of decisions and making them more timely and well-informed. Thanks to the identification of recurring patterns and emerging trends, AI makes it possible to anticipate citizens’ needs and plan targeted interventions, with a more strategic use of resources. - Personalization of services:
Through intelligent data analysis, AI enables Public Administration to adapt services to the specific needs of citizens, offering more personalized and effective experiences. In this scenario, AI Agents play a key role by providing immediate assistance and real-time responses, making interaction with the PA more direct, intuitive, and satisfying for the user. - Strengthening of transparency and public accountability:
Artificial intelligence can contribute to administrative transparency by automating data dissemination and simplifying the analysis of institutional activities. It allows citizens to access clear and understandable information, fostering greater awareness and transparency. - Combating corruption and promoting integrity:
Thanks to its ability to process large volumes of data, AI represents a strategic tool in preventing corruption. Real-time analysis of information flows allows the identification of potential irregularities and timely intervention, promoting a proactive approach based on transparency, control, and legality.
An example of AI application for the PA
Artificial intelligence-based tools offer a strategic contribution to the automation of complex and repetitive processes within public services, with particular relevance in document management. AI allows the optimization of workflows related to mandatory institutional services and administrative activities, significantly improving operational efficiency and access to information.
A concrete example of application is the automation of Certified Email (PEC) management: some PAs have adopted an AI-based system capable of automatically processing incoming PECs. These solutions enable the registration of applications and communications by detecting keywords, classifying documents, and associating them with the correct files, optimizing processing times and significantly reducing the risk of error.
AI Agent Margot for Public Administration
Margot is an intelligent agent based on artificial intelligence, designed to support daily activities and dynamically adapt to operational needs, seamlessly integrating into existing workflows. It is an advanced solution, created to simplify complex processes and increase efficiency.
Thanks to its modular architecture, scalability, and ease of configuration, Margot represents a strategic innovation that can be easily implemented even in the context of public administration, effectively responding to the new challenges and needs of the sector.
Discover more about AI Agent Margot
RAG (Retrieval-Augmented Generation): What it is and how it enhances AI
What is Retrieval-Augmented Generation (RAG)?
Retrieval-Augmented Generation (RAG) is an artificial intelligence (AI) process designed to optimize the responses of a traditional large language model (LLM). To achieve this, it references an external and reliable knowledge source, in addition to the data used during training, before generating a response. When providing answers, a RAG system draws from specific knowledge bases defined by the developers of the AI agent.
This technology combines the ability to retrieve relevant information from external sources with AI-generated text, improving accuracy and relevance. It enables organizations to leverage the power of LLMs by integrating their own documents, files, or web pages into the response process, ensuring more reliable and personalized results.
Practical Applications of RAG (Retrieval-Augmented Generation)
The practical applications of Retrieval-Augmented Generation (RAG) are expanding, thanks to its ability to integrate specific and up-to-date knowledge directly into decision-making and communication processes.
Some of the most relevant use cases include:
- Customer Support
RAG enables the development of intelligent chatbots capable of accurately responding to customer inquiries by drawing from manuals, FAQs, and company documentation. This reduces problem resolution times, enhances support efficiency, and ensures accurate, context-aware responses - Information Generation
This technology allows for the extraction of relevant data from business documents, annual reports, and other internal sources, facilitating quick access to strategic information and improving overall comprehension.
At the enterprise level, RAG allows organizations to leverage AI by grounding generative results in their specific business knowledge, delivering relevant and value-added responses.
What are vector databases in RAG and how do they work?
Vector databases are advanced storage systems designed to store and query vector embeddings—numerical representations of data, such as text or images, that capture their semantic meaning in a multidimensional space.
Here’s how vector databases function within Retrieval-Augmented Generation (RAG):
- Building the Archive: Before an LLM can retrieve external information, it must be processed into a format the system can understand. The first step involves transforming documents, web pages, or other databases into numerical representations called embeddings using specialized language models.
- Optimized Storage: Once created, these embeddings are stored in a vector database, which is designed to efficiently manage large volumes of vector data and enable rapid queries based on semantic similarity.
- Intelligent Search: When a user submits a query, it is converted into an embedding vector using the same language model employed for stored data. The RAG system then compares this vector with those in the database, performing a similarity search to identify the most relevant content for the user’s request.
- Semantic Search: Vector databases play a crucial role in implementing semantic search within RAG systems. Unlike traditional keyword-based searches, semantic search leverages embeddings to understand the meaning and context of queries, returning relevant information even when it does not contain the exact terms used by the user.
Benefits of using RAG over traditional LLMs
The use of Retrieval-Augmented Generation (RAG) offers several significant advantages over traditional large language models (LLMs).
Here are the key benefits of RAG compared to conventional models:
- Higher Accuracy
RAG generates responses based on reliable and up-to-date data sources, significantly reducing the risk of the LLM producing incorrect information. By providing a set of citable and verifiable sources, RAG enhances the trustworthiness of the information delivered. - Up-to-Date Information
Unlike traditional LLMs, RAG allows for the integration of continuously updated content, such as recent research, statistics, or real-time news. Information sources can be modified by adding or removing documents, improving the system’s flexibility and effectiveness. - Greater Control for Developers
With RAG, developers have more control over the generated text output, allowing them to customize and optimize responses based on specific needs. By refining and adjusting the information sources, the system can be tailored to different contexts, ensuring that generated results are relevant and aligned with application requirements.
Discover the solutions offered by E-time
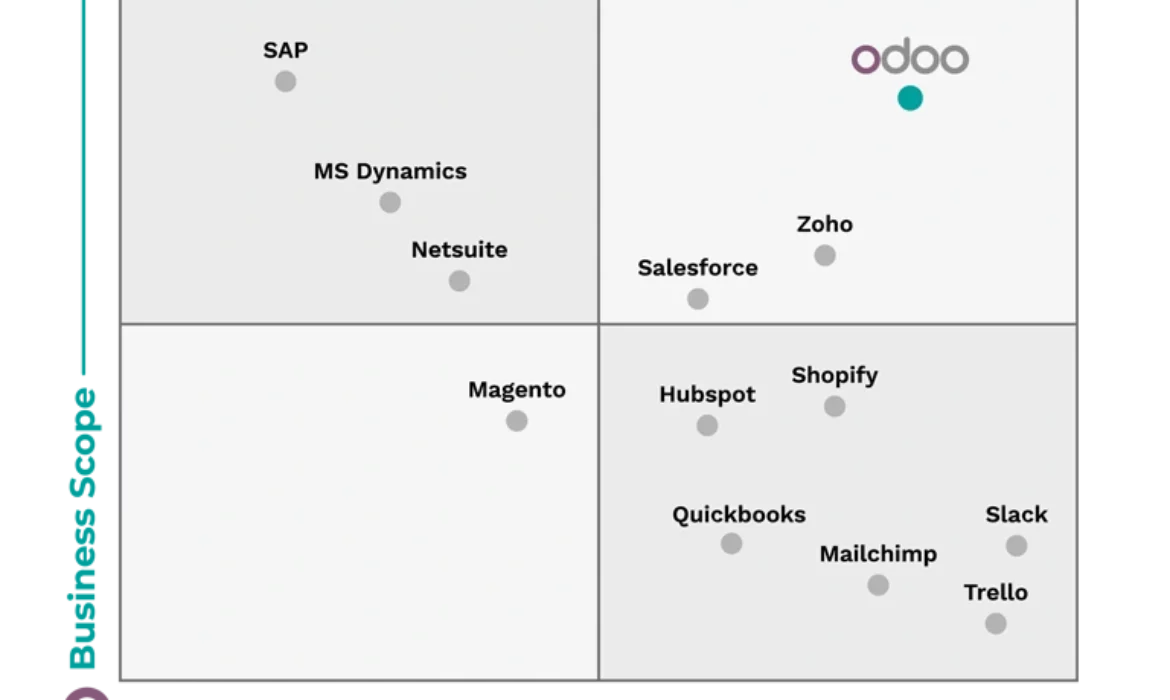
Odoo vs Salesforce: 5 reasons to choose Odoo
Salesforce represents one of the historical brands among the CRM systems in the market, while Odoo is a relatively recent player (relatively, because the software’s origin although significantly different from the current product dates back to 2005).
In recent years, Odoo’s growth has surged, primarily due to the multitude of Apps made available to users and its aggressive pricing strategy. In 2021, the company officially joined the ranks of “Unicorns” meaning companies valued at over 1 billion dollars. This is why we can now comfortably compare Odoo and Salesforce.
Odoo and Salesforce: a Comparison
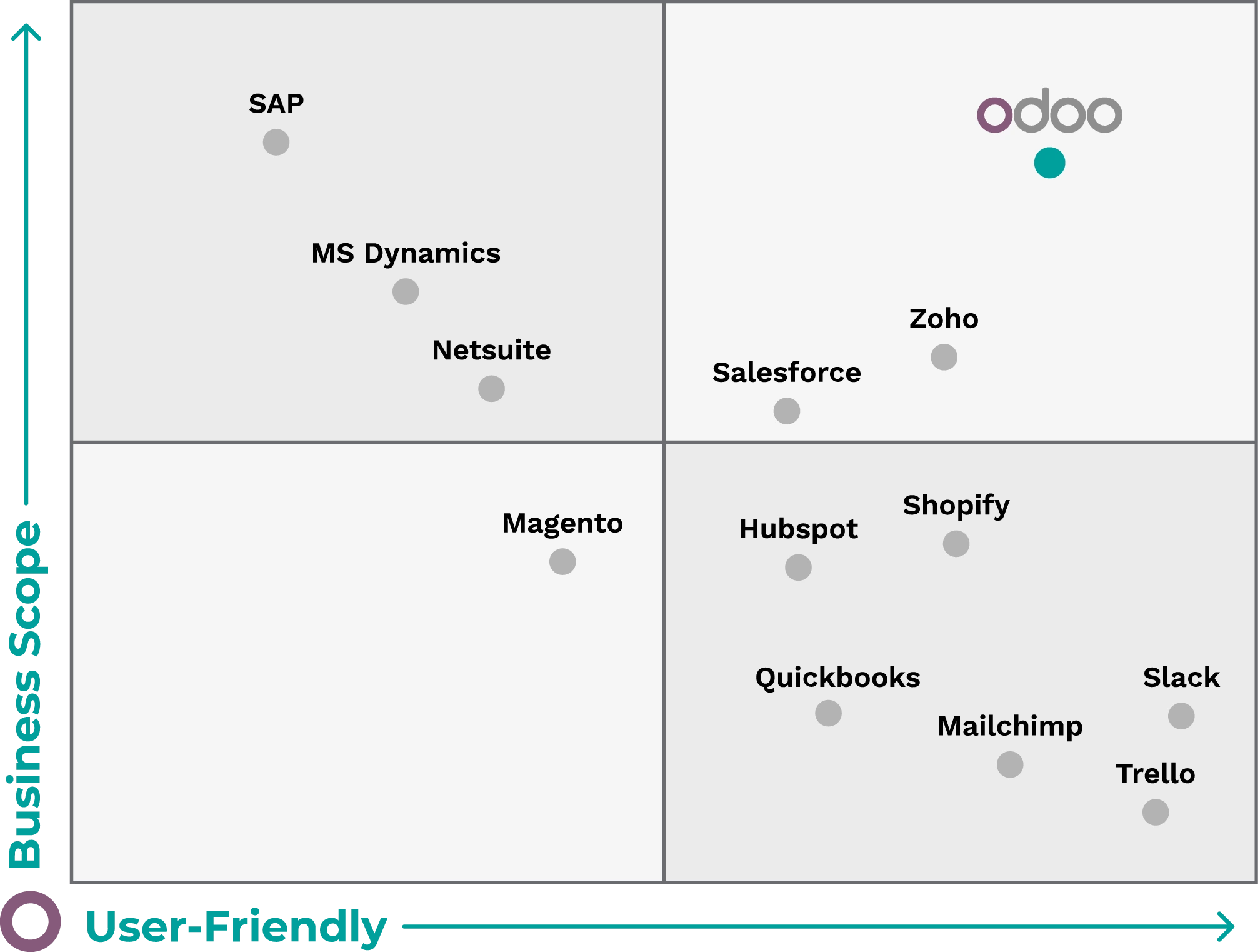
A necessary premise: Salesforce is a CRM software, whereas Odoo is an ERP software that encompasses various modules catering to different business areas (HR, accounting, warehouse, production, etc.).
Indeed, there would be nothing unusual about using both Salesforce and Odoo by integrating them, but let’s get to the point.
[INDICE]
1. Integrated System
Starting with the aforementioned difference, Odoo contains multiple applications (modules) such as CRM, Human Resources, Website, accounting, warehouse, and more – all integrated with each other. This eliminates the need to purchase and configure additional integrations.
2. Agile Customization
One of Odoo’s strengths is undoubtedly its high degree of platform customization, a characteristic likely stemming from the open-source logic around which the software was developed.
Odoo enables customization of the interface, modules, and workflows according to a company’s specific needs without requiring integrations with third-party software.
3. Scalabilità
Odoo’s architecture makes it a highly scalable system. You can start with 2-3 modules and then expand the scope of functionalities, adapting the software to the company’s needs. Unlike Salesforce, which might incur higher costs as a company’s needs grow, Odoo is suitable for startups or, more generally, for companies with evolving and growing structures.
4. Open Source and Accessible Code
Odoo was born and owes its development to the Open source formula. Odoo maintains a Community version (Open source), but it ensures a considerable degree of customization even in the Cloud version. It provides Partners and developers with the odoo.sh platform for code and functionality development and testing before production deployment.
5. Costs
What makes Odoo appealing to many entities is undoubtedly its cost. Odoo Community Edition is free, while the cloud version entails a monthly or yearly fee starting from 11.90€/user/month, along with a range of advantages and functionalities not present in the Community version.
A price point that is undoubtedly highly competitive, especially when considering that you’re not just purchasing a CRM but an ERP software.